Our safety features at a glance

Simple Login Experience
When using the Tapkey App, our users have the choice between username/password based login or well-established virtual identities like the Google account or Apple ID, giving all the world-class protection already built into these technologies.

Delegierte Authentifizierung
Wenn unsere patentierte Technologie in eigene Apps integriert wird, können Kunden ihre eigenen OAuth-Identity Provider mit Tapkey verbinden und somit die notwendige Sicherheit und Flexibilität gewährleisten.
Tapkey Lock Control Protocol
Tapkey is reviewed and continuously improved by trusted experts. The Tapkey Lock Control Protocol is our application layer protocol used for communication between locks and external devices, like smartphones or NFC transponders.

Geschützte, digitale Schlüssel
Wir tun alles, um deine digitalen Schlüssel zu schützen. So werden Schlüssel individuell für jedes einzelne Gerät vergeben und nicht wiederverwendet. Schlüssel sind beschränkt gültig, und können jederzeit widerrufen werden.

Stable & Scalable Backend Infrastructure
Our highly scalable cloud infrastructure is hosted in European data centers with high security standards. We are continually implementing state-of-the-art protection measures against attacks and have monitoring for early detection of problems in place.
How we protect your data
Tapkey boasts several layers of security. We’re using SSL/TLS encryption protocols for data transfer, while permissions are stored in the Tapkey Trust Service to ensure utmost security.
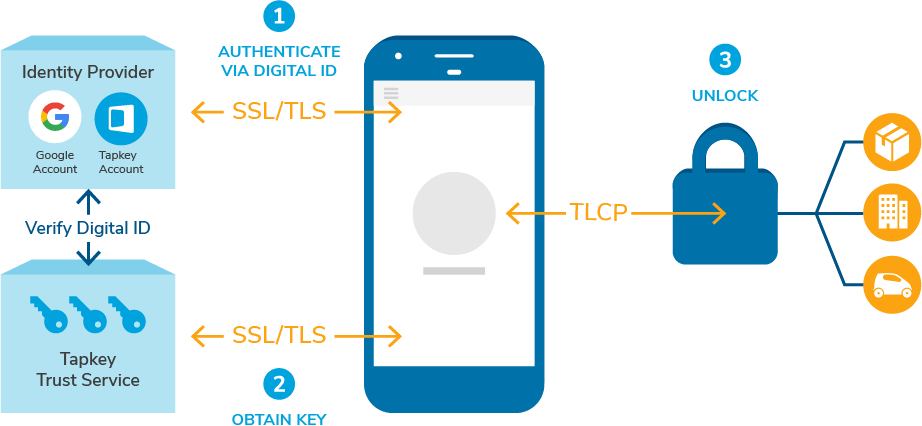
Tapkey and security at a glance
Always up-to-date
Although we try to build a high quality and secure product, we know that nothing is perfect. If you find a security problem in one of our products, please let us know! We follow a responsible disclosure policy. Hence, we like to work together with external security researchers that have found flaws in our products to resolve them and publish information about the vulnerabilities to protect our customers. If you want to report a vulnerability, please contact us at security@tapkey.com.
We have summarized general information about the security of the Tapkey system in a whitepaper. Just subscribe to our newsletter.
Tapkey’s production systems are not affected by CVE-2021-44228. VE-2021-44228 is related to a critical vulnerability of Apache’s Log4j logging component that could allow attackers to execute arbitrary code on affected systems. Tapkey’s production systems are not affected by CVE-2021-44228. The Tapkey Trust Service doesn’t use Log4j in any way and therefore isn’t affected by the vulnerability. The Tapkey Mobile SDK and the Tapkey App do use the Java language but don’t use Log4j. Moreover, the targeted operating systems (Android and iOS) don’t support JNDI, which would be required to exploit the vulnerability. The Tapkey Lock SDK isn’t affected, because it doesn’t use Log4j or the JVM in any way. That said, we did identify one non-production component that references a vulnerable version of Log4j. We do host some example code for Java developers on GitHub, which can be found here. The code uses spring-boot in a version that references a vulnerable version of Log4j. This sample code isn’t directly affected by the vulnerability by default, because even though it references Log4j, it is not configured to use it. However, we updated the sample to make sure a fixed version of Log4j is being referenced. Customers that use our Java example code as a basis for their own components are suggested to update their code accordingly.
Our constant commitment to maintain the highest security levels for our systems is in our company’s DNA and at the heart of everything we do. We’re therefore particularly delighted that this has also been recognised by external experts. Tapkey is officially SySS Security Approved!

At Tapkey, we are often asked by our customers if Tapkey is also affected by this type of attack on the Bluetooth technology standard. The short answer: It is not and never has been.










